Forensics
- Hidden in the traffic - 200
Hidden in the traffic
The challenge provides a PCAP. It notes that “the flag is hidden within the data.”
Examining the PCAP in Wireshark reveals some uninteresting DNS requests, QUIC traffic, TLS web communications, and a huge block of ICMP traffic:
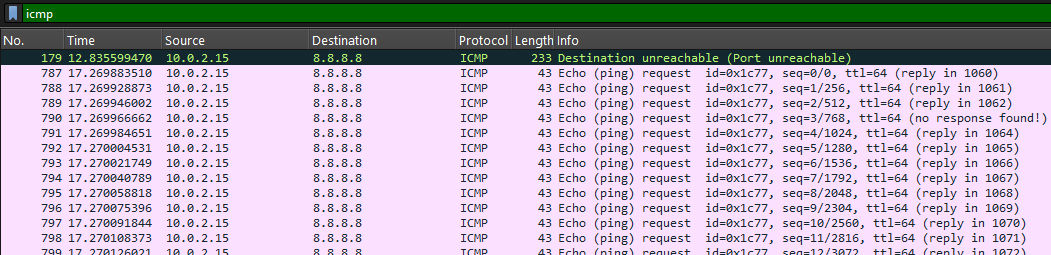
Each of the ICMP requests has a one byte data payload:
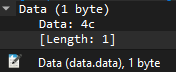
Using tshark, these data bytes can be extracted and converted to ASCII:
$ tshark -r Very_mysterious_file.pcapng -T fields -e data.data -Y 'icmp.type == 8' | xxd -r -p
AABCDEFGHIJKLCABCDEFGHIJKLE...ABCDEFGHIJKLhABCDEFGHIJKL}ABCDEFGHIJKLThere are characters that resemble the structure of a flag (braces, underscores), and appear to be padded with a static uppercase string. Highlighting the string illustrates this:
AABCDEFGHIJKLCABCDEFGHIJKLE...ABCDEFGHIJKLhABCDEFGHIJKL}ABCDEFGHIJKLAdding a chained command to strip this string allows for a one-liner that returns the flag from the original PCAP:
$ tshark -r Very_mysterious_file.pcapng -T fields -e data.data -Y 'icmp.type == 8' | xxd -r -p | sed s/ABCDEFGHIJKL//g
ACECTF{redacted}