Miscellaneous
- Sanity Check - 200
- Insanity Check - 200
- Rogue Insider - 300 - Unsolved
Sanity Check
The flag for this challenge is the channel topic for the #rules channel in the ACECTF Discord server.
This can be seen from, e.g., the Browse Channels page in the server:
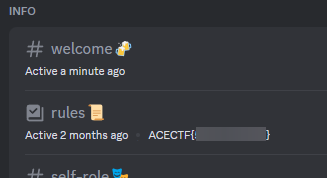
Or, from the #rules channel directly:
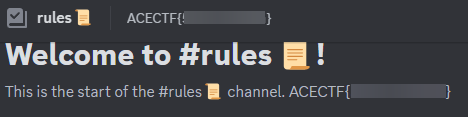
Insanity Check
Two hints were released for this challenge:
You might have found this weird string “r8F53sXv,” but who owns it?
Did you guys notice some weird roles in the server? Are they supposed to mean something?
By manually browsing through the list of members in the ACECTF Discord server, the following user with the role r8F53sXv can be found:
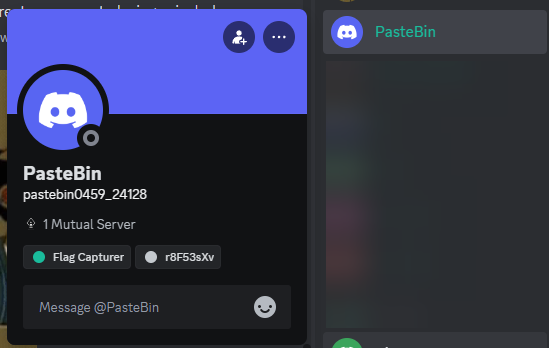
This provides a hint that the role string is a Pastebin ID. Visiting https://pastebin.com/r8F53sXv reveals the challenge flag:
You found Mr. Paste Bin!
ACECTF{redacted}Rogue Insider - Unsolved
The challenge provides a password-protected ZIP archive that appears to contain a Linux filesystem. The zip2john tool from John the Ripper can extract the hash of the password used to secure the archive. This can then be cracked with hashcat:
$ zip2john Log-In.zip
$zip2$*0*1*0...$/zip2$
...
$ hashcat '$zip2$*0*1*0...$/zip2$'
hashcat (v6.2.6) starting in autodetect mode
...
$zip2$*0*1*0...$/zip2$:kaliThus, the password for this archive is kali. It can be extracted for further analysis.
All top-level folders (etc/, home/, etc.) in the extracted archive have a last modified date of 2025-12-24. Searching for files modified after that date is an easy way to quickly scope to potentially interesting files:
$ fd . --newer 2024-12-25
etc/motd
home/linux/Downloads/
home/linux/Downloads/ASCII-Table-wide.svg
var/lib/nikto/
var/log/
var/log/alternatives.log.gz.zip
var/log/journal/2296c86330c3408caad86414c8b2e916/system.log
var/log/rotated_logs/The MOTD file states:
Notice: Check rotated logs for unusual ASCII activity.
The directory /var/logs/rotated_logs/rotated_logs/ contains archived.log.1.gz, which can be inflated with gunzip for analysis.
The log contains “Archived log entry XXXX” messages:
[2024-12-24 00:01:49] WARNING: Archived log entry 9326
[2024-12-24 11:07:49] WARNING: Archived log entry 7102
...
[2024-12-24 14:41:49] WARNING: Archived log entry 2156
[2024-12-24 12:38:49] WARNING: Archived log entry 4568There is a cronjob at /etc/cron.d/suspicious_cron:
* * * * * root echo 'Investigation required for /var/log/system.log'There is only one system.log in the challenge files (found with fd), at /var/log/journal/2296c86330c3408caad86414c8b2e916/system.log.
The file /var/log/application.log has the following snippet:
...
[2024-12-24 02:02:49] DEBUG: Hidden part 1: ACECT
[2024-12-24 07:04:49] DEBUG: Hidden part 2: F{thi
[2024-12-24 02:48:49] DEBUG: Hidden part 3: s is
[2024-12-24 07:08:49] DEBUG: Hidden part 4: the f
[2024-12-24 00:27:49] DEBUG: Hidden part 5: lag}There is a similar section in the system.log file noted above:
...
[2024-12-24 07:47:49] DEBUG: Hidden part 1: 00000
[2024-12-24 08:49:49] DEBUG: Hidden part 2: 84806
[2024-12-23 22:57:49] DEBUG: Hidden part 3: 42661
[2024-12-24 10:06:49] DEBUG: Hidden part 4: 46807
[2024-12-24 08:09:49] DEBUG: Hidden part 5: 60
...As seen during exploration with fd previously, there is an image ASCII-Table-wide.svg in /home/linux/Downloads/. This may be a hint, indicating these numeric logs are actually encoded ASCII messages.
Incomplete
No further progress on this challenge was made prior to the end of the CTF.
If continuing, next steps would be to further manipulate the numerals found in
system.log, using the provided ASCII table as a hint.